LAB 4-8: Virtual Private Network (VPN) – IPsec (Site-to-Site)
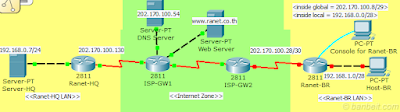
You are the Network Administrator at Ranet Branch Office, and have to newly configure the Ranet-Br router to let your own host connect to the internet and connect to the hosts in Headquarter (192.168.0.0/24) via Site-to-Site IPsec VPN as below:
(configure via console terminal for Ranet-BR router)
1. Enable LAN interface on Ranet-BR and set IP address to be the first assignable IP of 192.168.1.0/28 network.
2. Enable WAN interface on Ranet-BR and set IP address to be the last assignable IP of 202.170.100.28/30 network.
3. Set IP address on Host-BR to be the last assignable IP of 192.169.1.0/28 network, and set IP of Gateway and DNS server (202.170.100.54) also.
4. Config the route and NAT on Ranet-BR to let the Hosts in LAN connect to the internet (do not forget to exclude the VPN traffic).
(for NAT, use access-list no.100 and pool name “Ranet” that contain the global IP received from ISP as 202.170.100.9 – 202.170.100.14)
5. Config the Site-to-Site IPsec VPN by using the properties as below:
- For IKE phase I:- Policy Priority 101; Encryption Alg. AES-128 bit; Hash Alg. Secure HAsh standard; Authen method. Pre-Shared Key; Diffie-Hellman group #5 and lifetime at 86,400 sec. Use “ranetvpnpass” as key. Please note that IP address of WAN interface of Ranet-HQ is 202.170.100.130.
- For IKE phase II: Use Transform-set name “Ranet” and ESP transform using AES with HMAC-SHA as authentication Alg.
- Use crypto map name “Site-to-Site” with sequence no.101 and access-list no.101 to be the VPN traffic.
If everything is correct, Host-BR should be able to open website www.ranet.co.th, and test ping with Server-HQ 192.168.0.7 in Headquarter network.
Solution:
Ranet-BR config
(copy & paste these command below to Ranet-BR router.)
en
conf t
int fa0/0
no sh
ip add 192.168.1.1 255.255.255.240
ip nat inside
int s0/0/0
no sh
ip add 202.170.100.30 255.255.255.252
ip nat outside
exit
ip route 0.0.0.0 0.0.0.0 s0/0/0
access-list 100 deny ip 192.168.1.0 0.0.0.15 192.168.0.0 0.0.0.255
access-list 100 permit ip 192.168.1.0 0.0.0.15 any
ip nat pool Ranet 202.170.100.9 202.170.100.14 netmask 255.255.255.248
ip nat inside source list 100 pool Ranet overload
crypto isakmp policy 101
encryption aes 128
hash sha
authentication pre-share
group 5
lifetime 86400
exit
crypto isakmp key ranetvpnpass address 202.170.100.130
access-list 101 permit ip 192.168.1.0 0.0.0.15 192.168.0.0 0.0.0.255
crypto ipsec transform-set Ranet esp-aes esp-sha-hmac
crypto map Site-to-Site 101 ipsec-isakmp
set peer 202.170.100.130
set transform-set Ranet
match address 101
exit
int s0/0/0
crypto map Site-to-Site
end
Ranet-BR#sh crypto isakmp policy
Global IKE policy
Protection suite of priority 101
encryption algorithm: AES - Advanced Encryption Standard (128 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
Ranet-BR#sh crypto ipsec sa
ART-CNA-003-L48
interface: Serial0/0/0
Crypto map tag: Site-to-Site, local addr 202.170.100.30
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.240/0/0)
remote ident (addr/mask/prot/port): (192.168.0.0/255.255.255.0/0/0)
current_peer 202.170.100.130 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 202.170.100.30, remote crypto endpt.:202.170.100.130
path mtu 1500, ip mtu 1500, ip mtu idb Serial0/0/0
current outbound spi: 0x0(0)
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
Ranet-BR#copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
Ranet-Host
(Desktop > IP Configuration)
IP Address: 192.168.1.14
Subnet Mask: 255.255.255.240
Default Gateway: 192.168.1.1
DNS Server: 202.170.100.54
( Desktop > Command Prompt)
Packet Tracer PC Command Line 1.0
PC>ping 192.168.0.7
Pinging 192.168.0.7 with 32 bytes of data:
Request timed out.
Request timed out.
Reply from 192.168.0.7: bytes=32 time=32ms TTL=126
Reply from 192.168.0.7: bytes=32 time=31ms TTL=126
Ping statistics for 192.168.0.7:
Packets: Sent = 4, Received = 2, Lost = 2 (50% loss),
Approximate round trip times in milli-seconds:
Minimum = 31ms, Maximum = 32ms, Average = 31ms
PC>
(Desktop > Web Browser)
URL: http://www.ranet.co.th
Output: RANET Co.,Ltd. - Ranet Co.,Ltd. We make iT easy! :)
----------------------- The End ---------------------
Everything is OK.
You can view and download this solution here.
CCNA Lab
,
cisco
,
IT
,
Packet tracer
,
Practice Labs
,
Virtual Private Network (VPN) - IPsec (Site-to-Site)
,
WAN Technology
Để bắt đầu tham gia Giao dịch tài chính: